Resilient companies prioritize cybersecurity. And those that rely on a smooth-functioning supply chain are increasingly giving precedence to managing the cybersecurity risks of their suppliers, not just their own.
The catalyst for this shift is twofold. First, companies are recognizing the need for supply chain resilience as a result of the pandemic, geopolitical shifts, severe weather, and other recent events that have disrupted business. Second, cybersecurity attacks on corporate supply chains are growing in number, severity, and sophistication. According to the Ponemon Institute, 98% of companies have been negatively impacted by a breach that occurred at a company in their network. The long-term costs, including reputational and other damage to corporate value, can be high.
To maintain resilience in the face of cybersecurity risks in their supply chain, companies need greater visibility into, and influence over, vendors’ as well as customers’ digital systems and practices. Companies can make discernible improvements to their own resilience by implementing a well-crafted program that manages the cybersecurity risks of third parties in their supply chain.
Growing Risks, More-Sophisticated Attacks
To develop an effective risk-management program for a company’s supply chain, it’s important to understand why cybersecurity attacks are not only increasing but also increasingly successful.
The main reason lies in the complexity of companies’ supply chains and digital networks, which are often several tiers deep. For example, an auto manufacturer’s supply chain includes numerous vendors, manufacturers, service providers, and customers that rely on other suppliers, which, in turn, depend on still other vendors. The auto manufacturer’s many suppliers connect to its digital network, and they are also connected to their vendors’ and customers’ digital networks. In addition, the suppliers connect using an array of hardware and software components, which are sold and serviced by still other vendors. When a company operates a supply chain network with multiple tiers, third parties’ cybersecurity risks are also the company’s risks.
Another factor is the use of cloud networks. As supply chains grow, companies are investing in larger and more complex procurement networks, shifting workloads to public or private cloud networks. The shift is increasing companies’ reliance on cloud providers’ security controls and reducing visibility into risks.
The rapidly growing number of internet-of-things devices that are connected to networks is also a reason. The surge is creating numerous digital endpoints that can be entryways into a network. Since companies are relying more and more on electronic tools and devices, this risk is not likely to abate.
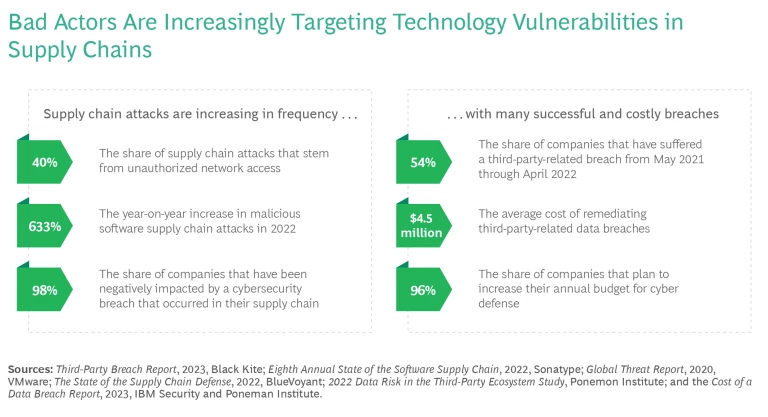
Finally, bad actors are using more-sophisticated tools and techniques to exploit vulnerabilities in digital networks, and weak points can be difficult to detect. Companies with established cybersecurity capabilities are being compromised through less sophisticated third parties that are connected to their network. (See the exhibit.)
One of the most sophisticated supply chain breaches occurred in 2020 because malicious code was embedded in the widely used SolarWinds software. The attack exposed the data of thousands of private companies and government agencies, mainly in the US and Europe. The supply chain attack spread quickly because the malware, which went undetected for years, infected software that was used to manage the affected organizations’ networks, enabling backdoor remote access to systems. A National Public Radio report called it “a hack unlike any other, launched by a sophisticated adversary who took aim at a soft underbelly of digital life: the routine software update.”
Other examples are the so-called Meltdown and Spectre vulnerabilities, which caused supply chain problems for companies worldwide. These attacks relied on flaws that were in the design of computers’ central processing units for years before being discovered in 2018.
A Proactive Approach
Despite the growing number of cyber attacks and their sophistication, the challenge of minimizing risks to digital networks is not insurmountable. Companies that take a proactive approach to managing supply chain cybersecurity can lower their risks and costs. (See “Rethinking Cybersecurity Outsourcing for a New IT Organization.”)
Rethinking Cybersecurity Outsourcing for a New IT Organization
To begin, the company reconstituted its IT organization and outsourced numerous services, including the management of the IT network, enterprise resource planning software system, and cybersecurity operations center.
The company also adopted agile vendor sourcing. Leaders detailed the decision-making criteria for choosing cybersecurity services and the requirements for selecting artificial intelligence and advanced analytics solutions. Company leaders also established new roles and responsibilities and crafted new service-level agreements that reflected the revised cybersecurity criteria and goals.
With the changes in place, the IT organization was better able to select vendors on the basis of their cybersecurity capabilities, balancing the speed of contracting with the quality of services. IT was also able to contract services at market prices. The result was a stronger defense against attacks and a 15% decrease in the cost of cybersecurity services.
Organizations have done this successfully by embracing a coordinated strategy that considers the organization’s needs as well as those of its suppliers and customers. Established practices include:
- Forming a collaborative senior leadership team that can secure buy-in across security, IT, procurement, legal, engineering, and other relevant functions, as well as make decisions collectively
- Establishing a formal, transparent, risk management program for the supply chain that has policies, processes, accountabilities, and a sufficient budget and staff
- Identifying and categorizing the company’s critical suppliers
- Determining which systems are critical to ensure accurate reporting of material weaknesses and significant deficiencies associated with third-party risk
In the face of the urgency and the size of the task, a proactive approach should include the following steps.
Get a risk management program in place. Many times, the hardest part is simply getting started. However, having a program puts a company miles ahead of organizations that have none at all. Begin by taking stock of the supply chain and identifying quick-win opportunities—weak points that can be addressed swiftly and yet make the network more secure. The solution will not be perfect. That is to be expected, not feared.
Companies that have a cybersecurity program are miles ahead of those that have none at all.
Develop the program as part of a broader risk management strategy. One way for a company to understand its degree of exposure is to develop scenarios for different types of cyber attacks on various types of suppliers. An organization should also identify the minimum amount of information it needs to have about its suppliers’ risk exposure in order to understand an attack’s potential impact on the supply chain and to assign each vendor to a risk tier. A more detailed risk assessment or stronger security controls may be warranted for suppliers in higher-risk tiers than for vendors in lower-risk tiers.
For example, a major consumer products company invested in a large-scale plan to implement cybersecurity risk-management practices in its supply chain. The practices included a technology-supported tiering approach that automatically prioritizes high-risk vendors according to cybersecurity-related tiering logic. The company used the approach to improve its sourcing processes and tools as well as to help customers and vendors strengthen their systems with minimal disruption.
Leverage the capabilities of existing tools. There may be existing, untapped capabilities within a company’s enterprise resource planning software and other systems that it can use to develop a risk management program. For example, consider incorporating a cybersecurity risk-tiering process or controls into the software.
Take a phased approach. In a large organization, the sheer number of third parties can be one of the largest roadblocks to implementing a risk management program. Rather than planning a rollout to all third parties simultaneously, a company could phase in a program by prioritizing regions, business units, or product lines—whichever areas have third parties that pose a higher risk. In addition, a company could pilot parts of the program with new customers and vendors or a select group of existing ones. For example, a new screening process could be tested with new vendors before being rolled out to other third parties. Information learned from the onboarding of new parties—especially about the common risks or vulnerabilities—can be used to assign risk tiers to the remaining parties.
A company could phase in a program by prioritizing regions, business units, or product lines that pose a higher risk.
Work across functions. Supply chain security cannot be improved by the technology or risk functions alone. Cross-functional teaming is critical to developing and implementing a risk management program for a supply chain. In addition to the technology and risk functions, leaders should involve the business units that are working directly with third-party vendors and customers, as well as the product, procurement, merchandising, and privacy functions.
Let the data drive the decisions. Companies should determine a way to evaluate the program and make adjustments accordingly. A good way to conduct an assessment is to identify vendors, before implementing the program, that agree to provide feedback. In addition, evaluate the program at regular intervals to gauge its effectiveness. The evaluation process may include analyzing sample data to ensure that third parties are assigned to the right tiers or that the process is assessing threat detail at the correct level, neither overanalyzing nor underanalyzing it.
Secure visible support and engagement from senior leadership. A cybersecurity risk management program for a supply chain can only be successful if senior leaders prioritize and support it with sufficient funding. For example, the involvement of leaders in tabletop cybersecurity risk exercises, possibly including engagement with third parties, can benefit the program by sending a clear message of its importance and by encouraging cooperation.
Cybersecurity risk is one the most important challenges facing organizations today. Thousands of companies suffer costly attacks related to third-party breaches each year. Supply chains and digital networks that have many tiers hinder companies’ visibility into their risks.
Companies that want to improve their supply chain resilience should initiate a cybersecurity risk-management program to strengthen the cybersecurity practices and policies of third parties in their supply chain. While embarking on such a program may seem daunting, it can be an especially effective way for companies to improve supply chain resilience and preempt organization-wide breaches.
The authors thank Nadya Bartol, Daniel Urke, and Chris White for their contributions to this article.





