This is the second in a series of articles and interviews on the subject of improving cyberresilience—the ability of companies, organizations, and institutions to prepare for, respond to, and recover from cyberattacks. To discuss how companies can maintain vigilance, BCG spoke with Yosi Shneck, the senior vice president of information and communication for Israel Electric, a company that has seen its share of cyberattacks. The series is a product of BCG’s work with the World Economic Forum. The first article examined how the federal government can assist at state and local levels with cybersecurity. Future articles will explore how boards of directors and senior managers should approach cybergovernance and how businesses undergoing digital transformation can ensure that cybersecurity is considered deliberately, rather than on an ad hoc basis.
About Yosi Shneck
Yosi Shneck is senior vice president of information and communication at Israel Electric. In addition, he is the chief information officer, overseeing the ITC and Broadband Communication divisions, and the chief compliance officer, managing the cyberreadiness organization.
Shneck has spent more than 40 years in the utility industry, and his knowledge of computer systems and technology includes experience with information systems, scientific applications, supercomputing and communication, control systems, infrastructure and architectures, and cybersecurity.
As chief compliance officer, he is responsible for preparing the company for cyberattacks, including ones that target the company’s information technology and operational technology environments. Given the importance of securing critical infrastructure, Shneck is involved in many cybersecurity initiatives nationwide.
Shneck joined Israel Electric in 1995 and has held many positions, including head of the Information Systems and Communication division, head of the National Communications and Electronics unit, and deputy of the Information Systems and Teleprocessing division. He also served as a member of the selection committee that was seeking an investor in a new communication infrastructure company.
Shneck has an MBA and a BSc in computer science.
Read more in the Cybersecurity Series
- The Cybersecurity Assistance Local Governments Need
- Cybergovernance and the Role of the Board: An Interview with Kaiser Permanente’s George DeCesare
- Giving Cybersecurity Its Due in the Boardroom: An Interview with Standard Chartered’s Cheri McGuire
- Advancing Cyberresilience in the Electricity Ecosystem: An Interview with Iberdrola’s Rosa Kariger
Can you share some of what you’ve learned about managing an organization that is constantly addressing advanced, persistent threats?
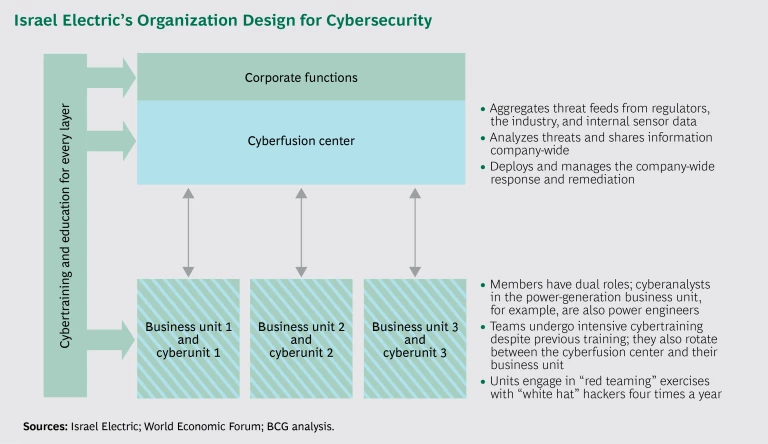
I think there are two things that we do that are perhaps uncommon. First, we don’t separate our operational technology (OT) and information technology (IT) environments. Many companies do, but this is a mistake! The target of the attackers is the OT system, but the highway is the IT system. Second, we have a distributed yet integrated organizational model for cybersecurity. The distributed part is this: every business unit has its own cyberunit with its own local security operations center, its own local response team, and its own cyberanalyst.
Every business unit has its own cyberunit with its own local security operations center, its own local response team, and its own cyberanalyst.
Everybody in a cyberunit has two sets of competencies: one in business process and another in cybersecurity. For example, the members of the cyberteam in our power-generation business unit are power station engineers with advanced cybersecurity skills. The distributed business units and cyberunits are integrated in a cyberfusion center, which collects data that comes not only from cyberunits but also from government regulators and intelligence, equipment sensors, and other unique information sources. All the data is analyzed using high-level analytics models and techniques. The cyberfusion center is responsible for creating a continuous, real-time picture of the organizational cybersituation and supporting the distributed cyberunits in any situation, whether it’s routine or an emergency. (See the exhibit.)
We also believe in cybersecurity by design. That is, the cybersecurity aspect of everything should be understood and taken into account at the design stage. To this end, we have mapped out most of our business processes and screened them for the cybersecurity aspect. For example, if we want to change a procurement policy, it is screened by the cyberrisk side, and proper cyberdefense prerequisites are considered from the initial stage and across the whole process. If we want to change a recruitment process, it’s the same thing.
Cyberdefense, like most other issues, depends on three main factors: people, policies and processes, and technology. And people are the weakest link. At the end of the day, most issues can be ameliorated if people act better. For that, we decided to train, train, train. We invest a lot in training people—even if they come from the army or secret service and have extended experience in cyberdefense. And not only cyberprofessionals are trained. Management, office workers, technicians—everyone receives cybertraining.
Why is Israel so effective at securing critical infrastructure? Are there particular policies that the country has pursued to make its critical infrastructure more resilient?
It’s not so much about policy but about the independent, self-reliant mindset that is the result of our geopolitics. Living in an environment of tension has created the belief that you have to be prepared for any scenario and depend on yourself as much as possible.
With that said, it’s important to be honest. These cyberevents really happen, and the risk is always there. Of course, I don’t sleep well as result of that, but I know that if something happens, it is my responsibility, and I must be prepared for it to the greatest extent possible. There is no other option, other than to deal with it.
Many countries have grappled with the difficulty of whether to assign responsibility for securing critical infrastructure to civilian or military organizations. Israel seems to have navigated this tension—security has been deemed the peacetime responsibility of the Israeli Security Agency (Shabak) rather than the Israel Defense Forces. Are there any lessons from that arrangement for other countries trying to facilitate public-private cooperation?
There are a few principal players in Israel: the National Cyber Bureau, the secret services, the army, and the nondefense stakeholders (civil enterprises and organizations, for example). The main lesson that all these organizations have applied is that it is highly important to avoid having any borders or barriers between or among them. They all foster a high level of cooperation among their technical, functional, intelligence, and knowledge layers. They use common and frequent communication protocols and channels to cooperate at every level.
The main lesson is to foster a high level of cooperation among the technical, functional, intelligence, and knowledge layers.
We recently moved, as a result of a government decision, toward a civil authority for regulating civil entities, and we are finding benefits in this arrangement. Civil authorities understand civil processes; they appreciate and understand the culture and management of commercial companies, both of which are different from those of military or secret service authorities. The military and defense agencies can apply their deep knowledge and expertise in the background when needed.