The way a government stores, manages, and protects the vast volumes of sensitive data in its keeping and expands its digital capabilities and footprint to better serve its population are arguably its most critical functions in today’s networked world. But this is increasingly a more difficult and confounding task.
Managing government databanks in global cloud-based environments is the obvious solution, but not a good one. Compliance with local data protection laws as well as international regulations that potentially give foreign law enforcement agencies access to a government’s private information complicate data security strategies on these networks. In addition, cyberthreats on large open-ended networks are a significant and ongoing problem, requiring governments to formulate ways to shield their most sensitive information involving government operations, national infrastructure, national security, and economic policy from online criminals.
Given these data protection challenges, many governments are smartly seeking new ways to avoid typical cloud-based platforms for their sensitive data. Instead of entrusting this information wholesale to large global cloud providers, or hyperscalers, located outside the jurisdiction of the countries they serve, governments are developing internal systems—albeit often with the help of hyperscalers.
Stay ahead with BCG insights on digital, technology, and data
The Emergence of Sovereign Clouds
These networks are called sovereign clouds. At its core, this model is designed to guarantee that sensitive information is held within the jurisdiction of the country whose data is on the network. It is built around technological and operational sovereignty in the network host country and insulates the data from geopolitical conflicts and global cloud network outages. And perhaps most importantly, it is meant to ensure that a nation’s digital assets are controlled locally in a stable and secure environment for critical national data and are protected against international legal entanglements.
Indeed, one of the primary catalysts for adopting sovereign clouds is the 2018 US Cloud Act. This law allows American law enforcement authorities with a warrant during a criminal investigation to access data stored by US-based cloud providers—among them, Amazon, Microsoft, and Google, the top three global hyperscalers—even if that data is located outside the US. However, the law includes a provision enabling providers to challenge the warrant in court if the data sought does not pertain to US citizens and if providing the data would contravene the laws of a foreign government. Despite these provisions, some governments are designing sovereign clouds with sufficient degrees of domestic data and operational autonomy to be certain that they are off limits to US jurisdiction.
Beyond security and compliance, sovereign clouds also offer significant economic benefits. By localizing cloud infrastructure, countries can create high-quality, technology-based jobs and enhance the skill set of their local workforce. Developing local expertise in cloud technologies ensures that countries are better positioned to innovate and adapt to future advancements, fostering a self-sustaining digital ecosystem.
Keys to a Successful Sovereign Cloud
As nations navigate the complexities of digital transformation, building a successful sovereign cloud requires a carefully designed framework that balances hosting data locally while strategically aligning infrastructure, governance, and operational principles to ensure security, compliance, and innovation. BCG research has shown that achieving this hinges on meeting eight critical criteria.
- Infrastructure control and ownership. Ensuring that the physical data centers and hardware are owned or sufficiently controlled by local entities to prevent foreign influence and unauthorized access.
- Data residency and compliance. Guaranteeing that all data is stored and processed within national borders and adheres to local data protection regulations.
- Data segregation and isolation. Ensuring that sensitive government and national infrastructure data are physically and logically segregated from other cloud tenants and isolated to prevent cross-tenant access or interference.
- Data security and user privacy. Implementing robust cybersecurity measures, compliance frameworks, and data anonymization techniques to protect against data breaches and ensure adherence to national security standards.
- Operational control and training. Ensuring that the cloud operations, including system administration, monitoring, and maintenance, are managed by trusted personnel with appropriate security clearances and continuous training.
- Service quality and reliability. Combining high-quality service delivery with minimal downtime, supported by disaster recovery plans and resilience against geopolitical disruptions.
- Transparency and governance. Establishing clear governance processes with transparency in cloud operations and decision making to build trust and accountability.
- Scalability, innovation, and interoperability. Providing scalable cloud solutions that can adapt to growing demands, foster innovation through state-of-the-art software and platform tools, and ensure interoperability with other cloud services.
These criteria are both wide-ranging and essential. To adopt them as the foundation of a sovereign network, it is helpful to categorize them in three buckets: infrastructure, operations, and software and platform.
Infrastructure
This refers to the data center and the physical hardware, including servers, storage systems, and network components that make up the cloud environment. Broadly speaking, ownership of the infrastructure ultimately governs whether foreign authorities can gain access to the network data. In short, locally controlled infrastructure is crucial to protect against unauthorized outside access and ensure compliance with domestic regulations.
Operations
This is defined as the people and processes that operate and maintain the cloud environment. This includes everything from system administration, monitoring, and maintenance to incident response and compliance management. Governments can take the lead in this set of activities, but they must be painstaking in establishing high standards for the background, training, and loyalty of the engineers who manage the cloud environment, as well as their access privileges. Ensuring that operations are conducted by trusted personnel with proper security clearances is essential for maintaining data integrity and transparency. Effective operations also require strong cybersecurity measures, disaster recovery plans, and regular audits to ensure the cloud environment remains secure and reliable.
Software and platform
This covers the applications, services, and development tools that enable data processing, storage, and analysis on the cloud. This is the component of sovereign networks in which hyperscalers should play the largest role. They can continuously provide state-of-the-art software programs and platform tools that support greater efficiency and the ability to innovate. Moreover, they have proven capabilities in delivering advanced AI and machine learning tools, big data analytics, and seamless integration services. These are critical for governments hoping to leverage their data for insights and innovation. Ensuring that these platforms are technologically advanced, compliant with local data protection laws, and capable of being customized to meet specific national requirements is crucial for successful sovereign clouds.
The Role of Hyperscalers
Compared to putting the pieces together to develop an efficient, secure, and agile network, identifying the criteria for a successful sovereign cloud is easy. Although working with hyperscalers requires substantial effort to ensure the right amount of local autonomy and limited foreign government interference without sacrificing performance and potential innovation, the other option—do it yourself—is a non-starter.
Virtually no governments have access to the expertise needed to set up secure and resilient cloud environments able to keep pace with the rapid advancements in data analytics, artificial intelligence, and machine learning that will transform these networks in the coming years. Nor are many governments prepared to shoulder the high initial investments and ongoing operational expenses, and they are not equipped to reduce costs over time through economies of scale. Additionally, the burden of ensuring compliance with constantly evolving data protection regulations can be overwhelming for in-house teams.
Given these shortcomings in most countries, partnering with hyperscalers is the sensible solution. But governments are then faced with the question of balancing the need to leverage the software and platform tools that these companies have refined with the criteria required for secure data sovereignty. Obviously, different governments—depending on their technological maturity, data sensitivity, local privacy regulations, and geography—will come to their own conclusions for dealing with these trade-offs.
Two Models Are Prevalent
Although the first sovereign clouds appeared in 2019, countries in every region of the world have already implemented these platforms. Among the notable early adopters are Germany, France, China, the Netherlands, Sweden, the UAE, Italy, Singapore, Brazil, Canada, and Israel. In all these cases, partnerships with hyperscalers are routine, but they take different forms. These arrangements can be divided into two models, each with different benefits and disadvantages. (See the exhibit.)
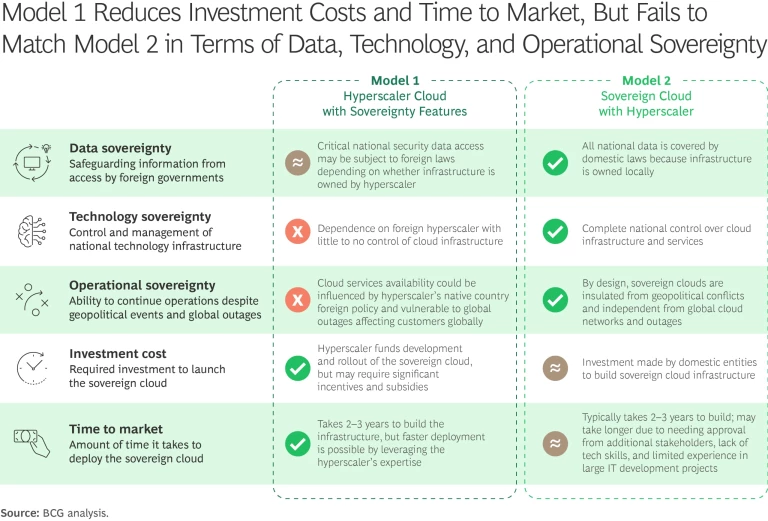
Model 1: Hyperscaler Cloud With Sovereignty Features
In this approach, the cloud infrastructure and operations are controlled by the hyperscaler. With their expertise in infrastructure and operations management, these global cloud providers can claim to offer high-quality service at lower costs for government networks. Moreover, these partnerships provide governments access to cutting-edge technologies, such as AI and analytics, enabling faster innovation. They also can be deployed relatively quickly, making them attractive for governments needing immediate solutions. In many cases, hyperscalers include “confidential computing” features that isolate and protect sensitive data even in the more public environment of the cloud, which may be shared by any number of organizations.
By choosing Model 1, governments can avoid initial investments and ongoing business risks. However, fundamental security and data protection issues remain, as the infrastructure and operations are managed by foreign entities and, hence, subject to their rules covering if and when data can be retrieved by law enforcement and other authorities. One way that governments have tried to get around those potential incursions is by building dedicated data centers within their countries, but legal experts differ on whether that is sufficient to protect the data from foreign access. Additionally, this implementation offers limited knowledge transfer and economic benefits for the local workforce. But hyperscalers favor this model because it protects their intellectual property and minimizes cannibalization of their public cloud business.
Singapore’s Smart Nation and Digital Government Group (SNDGG) is an apt illustration of this approach. In 2023, working with Amazon, Singapore IT authorities created so-called dedicated local zones in the country’s cloud environment that had enhanced data security to protect sensitive materials and records. Aside from this segregated and safeguarded data, accessible only by authorized staff, other facets of the sovereign cloud—including infrastructure, operations, and software—are essentially Amazon’s domain.
Model 2: Sovereign Cloud With Hyperscaler
In this model, the cloud is entirely disconnected from the hyperscaler’s global network. Local governments have complete control over the data, cloud infrastructure, and operations. The hyperscaler merely provides the technology backbone. This set-up ensures that sensitive information totally resides within the country’s jurisdiction, which ostensibly walls it off from external legal and cyber threats as well as geopolitical disruptions.
Model 2 creates local jobs and facilitates knowledge transfer. But legitimate concerns remain about reduced network quality and the potential lack of ongoing innovation and improvements—particularly as advances in AI and machine intelligence blossom—unless substantial resources are allocated for technical advancements. This model is also more expensive and complicated to implement and takes longer to design and develop compared to hyperscaler-controlled alternatives. Still, despite these downsides, this model is preferred by many governments and regulators who value the hyperscalers’ software and platforms but realize that local data management is critical for the success and security of sovereign clouds.
Germany chose this method in 2022 when it hired Arvato, a domestic company, to work with SAP and Microsoft on a sovereign cloud for the country’s public sector. Under the specs for this project, all data processed and stored is to remain in Germany and adhere only to local sovereignty regulations. The software and platform will be physically segregated from Microsoft’s global cloud network, although Arvato has promised to support upgrading these aspects of the system as needed. While this sovereign cloud model should be sufficient to secure sensitive information from foreign entities, having multiple partners involved in this project, including government players, is contributing to a somewhat slow rollout. Hence, the cloud is still not officially in operation.
Fashioning the Right Blueprint
Given the importance of protecting data from global law enforcement, Amazon’s AWS, Microsoft’s Azure, and Google Cloud are increasingly targeting technical fixes for the sovereign market that emphasize robust data segregation and hinders access by local authorities.
For instance, AWS is investing nearly €8 billion on a system designed to meet strict EU data residency and operational autonomy requirements. The company hopes to roll out its first version of this in Brandenburg, Germany, by the end of 2025.
Meanwhile, Google Cloud offers a so-called “air-gapped on-premises” managed approach for the most sensitive workloads requiring complete isolation from the public internet. The company also provides connected and virtual on-premises deployment models, which allow for direct links to its cloud. Google has already deployed the air-gapped approach in a number of public sector applications, including a sovereign network that features AI capabilities in Malaysia.
Finally, Microsoft has opted for localized partnerships, working with regional firms to meet country-specific security and compliance needs. For example, the company is collaborating with Bleu, a cloud service provider based in France, to offer Azure services in a fully sovereign cloud.
Keys to a Good Partnership
No matter which model a government chooses, the partnership it forges with hyperscalers could be the difference between success and failure. Given their significant expertise in platform operations and orchestration, hyperscalers should take the lead in much of the technology development and support—the DevOps—while local sovereign design, management, and control are maintained to a degree that is more than sufficient to protect the data. In order to nimbly skirt the balance required to establish the appropriate roles and responsibilities in sovereign cloud development, operations, and control, a series of fundamental rules should be followed.
- Set clear objectives. Define the goals, requirements, and operational expectations for the sovereign cloud environment, taking into account the legal and regulatory landscape that it will operate in.
- Select the right partners. Choose hyperscaler partners that are committed to supporting data sovereignty requirements. Seek providers that offer flexible solutions and are willing to work with local entities to comply with data mandates.
- Develop local expertise. Invest in building local teams with the skills and expertise needed to manage and support the sovereign cloud. This includes training and certifying staff in cloud technologies and data management practices.
- Implement robust security measures. Ensure that the sovereign cloud environment is secure and compliant with local regulations. This includes implementing encryption, access controls, and regular security audits.
- Foster collaboration and communication. Establish clear communication channels between local entities and hyperscaler partners. Regularly share updates, challenges, and successes to ensure all parties are aligned and can address issues promptly.
- Monitor and adapt. Continuously monitor the sovereign cloud environment to ensure that it remains compliant and the performance meets the goals for the network. Be prepared to adapt and update strategies as regulations and requirements evolve.
Implementing Sovereign Clouds
Governments must overcome a plethora of technical, financial, and operational hurdles to build a successful sovereign cloud. Perhaps the paramount issue is the high cost of sovereign cloud infrastructure, which includes data centers, hardware, and connectivity, alongside the ongoing expenses of maintenance and upgrades. Additionally, ensuring compliance with complex and evolving data protection regulations can add to the financial and administrative burden.
A related hurdle is the skills gap in many regions. Developing and managing sovereign cloud systems requires expertise in advanced technologies such as encryption, AI, and data analytics—fields where local talent may be lacking. This gap can slow deployment and make nations dependent on external providers.
Finally, forming effective partnerships adds another layer of complexity, in large part to future-proof the sovereign cloud. As digital needs evolve, sovereign clouds must be scalable and adaptable to emerging technologies, such as AI and quantum computing, without compromising security and control.
Despite these challenges, governments can adopt a series of strategies to smooth the path to implementation. They include:
Phased Deployment
Focus first on critical sectors, such as defense or healthcare, where sovereignty is paramount. This allows governments to refine their systems before expanding to less sensitive data.
Public-Private Partnerships
Collaborate with local firms or a hyperscaler to share the cost of building infrastructure while gaining access to advanced technologies. The Build-Operate-Transfer (BOT) model, in which private entities initially develop and operate the system before handing it over to local control, has proven effective in countries like the UAE.
Workforce Development
Create training programs jointly with academic institutions and companies, offering incentives for professionals to specialize in cloud technologies. For example, Singapore has successfully trained and upskilled thousands of individuals in cloud specialization through partnerships with hyperscalers.
Cybersecurity Measures
Prioritize advanced encryption, regular audits, and robust threat detection protocols to ensure that sovereign clouds remain resilient to cyberattacks. Some countries have implemented local encryption key management to ensure that hyperscalers cannot access sensitive data, even when they provide the underlying technology.
Sovereign clouds should be viewed not through the challenges they represent but rather the significant solutions they offer governments. They are a transformative technology reshaping the digital future of nations. By successfully building secure and resilient systems, governments open doors to extraordinary opportunities for economic growth, technological advancement, and strengthened sovereignty.






