Adoption of cloud services promises greater flexibility, increased scalability, and significant cost savings. Gartner estimates that by 2025 over 95% of new digital workloads will be deployed on cloud-native platforms. Often, however, companies don’t fully realize the cloud’s promise, with only 52% of organizations self-identifying as cloud-mature, according to 451 Alliance. Cybersecurity issues are often responsible for the slow pace of cloud migrations, with almost 50% of companies citing cybersecurity as their top concern.
That is because many organizations embark on cloud deployment without first creating a strategy for continually protecting their cloud-based infrastructure and data. Even worse, organizations commonly treat cloud deployment and migration as purely technology initiatives and assume that people and processes will simply adjust to the new reality. Constantly evolving cyber threats, the myriad cybersecurity technologies available in the market, and a persistent shortage of cyber expertise all compound the challenge.
The answer lies in creating a holistic cloud security strategy that aligns people and processes with the changes in technology that cloud adoption entails. The strategy is based on Secure by Design principles, which call for addressing security as early as possible in the overall deployment life cycle. It drives secure cloud operations by creating and automating a reusable set of security controls, known as security plans, during the initial (prebuild) phase of deployment. The process then iterates the security plans across the second (build) and third (monitor) phases, using further automation to support a self-optimizing system that lessens rework and boosts efficiency.
Scattered Security Planning Leads to Rising Costs
Security teams must master considerable complexity when working with cloud-based technologies. Cloud security activities often require input from multiple technical and security teams, each of which has its own priorities and may disagree on approaches. Teams must also deal with unfamiliar and rapidly evolving cloud-based technologies. Learning takes time that security professionals don’t have, a deficiency exacerbated by the global shortage of global cybersecurity talent, which leaves understaffed teams spread thin.
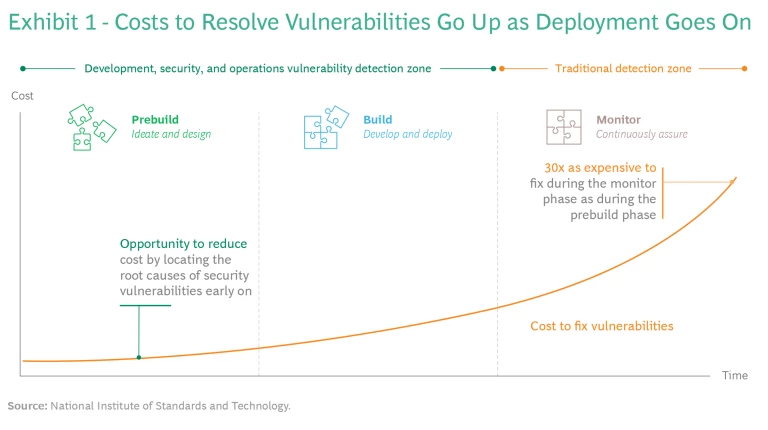
By forming and refining security plans earlier in the cloud development life cycle, organizations can identify vulnerabilities promptly and lower the costs of addressing them. Such costs grow exponentially as the life cycle progresses, meaning that the longer an organization waits to put adequate security controls in place, the more expensive the effort will be. According to the National Institute of Standards and Technology, vulnerabilities introduced in ideation and design are roughly 30 times as costly to resolve after deployment as when detected and fixed early on. (See Exhibit 1.)
Efficiency is crucial to a successful cloud migration. Nevertheless, some organizations take up to 100 days to complete the prebuild phase and still face challenges in the build and monitor phases. In the absence of a comprehensive strategy, teams must reinvent security for each new or changed application throughout these latter phases. Functions such as identifying security requirements, assessing risks, and approving designs become uneven and fragmented. Rework and duplicate effort cause delays for security stakeholders while costs keep going up.
To avoid these complications, teams should follow the principles of Secure by Design, or “shift security left.” By implementing standardized security plans at the beginning of the development cycle, organizations can enable teams to consistently apply and update them as necessary throughout the process. This approach also allows developers to apply the considerable strengths of infrastructure as code (IaC) to their use of automation, reducing manual efforts and enabling organizations to realize value throughout the build and monitor phases.
Automation Brings More Value
The rising costs and expanding complexity associated with cloud operations have prompted a shift toward automation through IaC. The goal of IaC is to manage reusable cloud infrastructure through code instead of through manual processes. In recent years, IaC has become the gold standard for mitigating many security challenges.
Through IaC, which is introduced during the build phase, developers can reuse secure configurations and components much more productively, leading to faster deployment of the company’s various cloud resources. During the monitor phase, developers can use IaC to increase scalability and strengthen automated reporting to monitor compliance with security requirements across all cloud deployments.
Cloud service providers and government entities have rushed to embrace this approach. In 2021, the US Department of Defense published its secure IaC repositories, playbooks, and hardened container images, which organizations can use to ensure better security. More recently, Amazon released a library of code templates to support the implementation of secure reference architectures in Amazon Web Services environments.
BCG clients have realized significant benefits by using IaC to secure cloud deployments. One company that created a centralized intake process and developed a set of preapproved security requirements and automated security plans saw a 300% improvement in time to deployment and an 80% reduction in overall developer time.
Such results are within the reach of any company willing to implement a Secure by Design strategy that uses IaC to facilitate automation. Automation relies on having mature, standardized processes in place that the organization’s staff can consistently perform. These processes provide rules and are monitored according to Secure by Design principles.
Subscribe to our Digital, Technology, and Data E-Alert.
Secure by Design Shifts Security Left Across Cloud Engagements
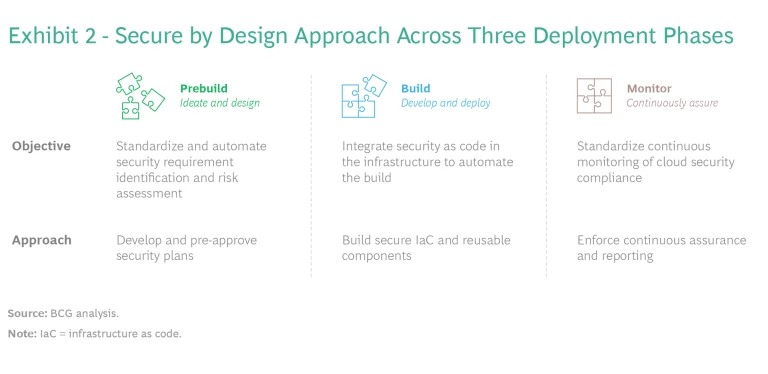
The Secure by Design approach aims to establish automated security processes that extend within and across each phase of the cloud development life cycle. By developing and codifying security controls during the prebuild phase, the business puts itself in a position to form comprehensive security plans. These plans promote efficiency throughout the development cycle, from ideation to continuous assurance. (See Exhibit 2.)
Organizations can start by tackling the four key steps of the prebuild phase:
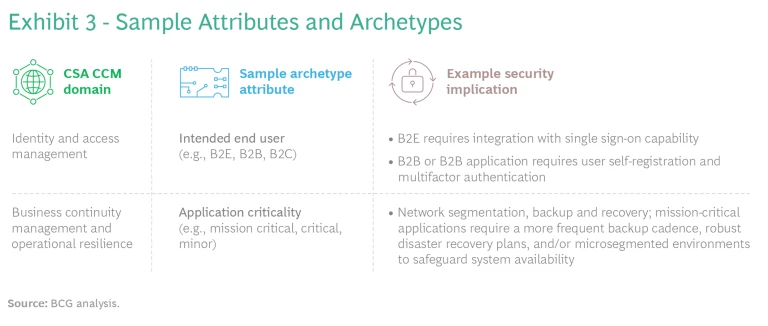
Define application security archetypes. The organization should group applications into archetypes. Teams can identify attributes or specifications that have security requirements in common, given their risk profile and business context. (See Exhibit 3.) When grouping applications into archetypes, teams should strive for alignment with a common framework, such as the Cloud Controls Matrix (CCM) created by Cloud Security Alliance (CSA). Financial institutions (FIs) can use the Cyber Risk Institute’s Cloud Profile, which harmonizes FI-specific security regulations and standards and was developed in alignment with CSA’s recently released CCM 4.0.
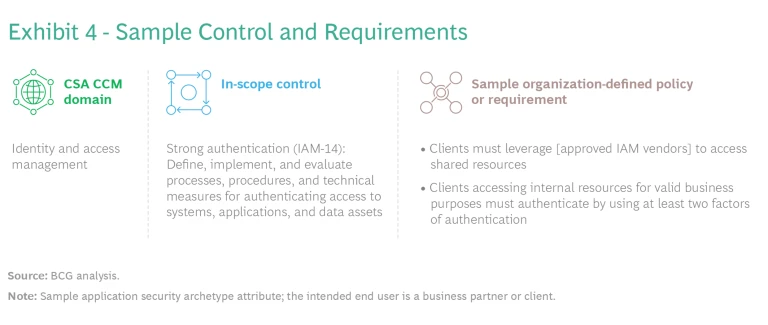
Identify in-scope controls, and define security requirements. After defining an archetype, security teams can identify security controls that are suitable for the group of applications. Teams should ensure that any requirements needed to satisfy the control comply with all relevant laws, regulations, and frameworks. In many cases, multiple requirements are necessary to collectively satisfy a given control. (See Exhibit 4.)
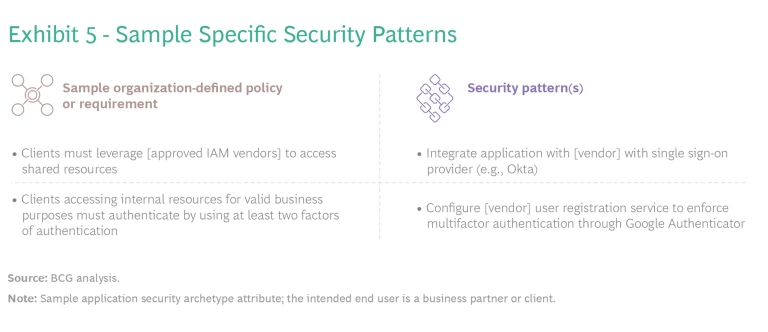
Draft security patterns. Security teams must draft security patterns matched to in-scope controls and requirements. Security patterns enhance security requirements by framing them as actionable descriptions that make sense to developers. Patterns must be specific enough to support automation in the build phase, such as through IaC. (See Exhibit 5.)
Preapprove security plan. The security plan consists of a comprehensive list of security requirements and patterns that users have gathered for a given application archetype. Owners of the security plan may circulate the requirements and patterns to various stakeholders for approval. Large organizations may seek approvals from an array of experts and assessors, including those involved with identity, business continuity, legal affairs, and human resources. Each stakeholder should verify that the plan will ensure compliance with internal organization policies and applicable regulations. The plan should also offer an accelerated path to development. In addition, the organization should establish prebuild objectives and key results and underlying key performance indicators to measure improvement and track return on investment over time.
The prebuild process can go further to encompass designing a centralized, automated cloud intake process that matches a common application’s attributes to a cloud security archetype. Product owners that input the new or changed application attributes receive a set of applicable and standardized controls, requirements, and security patterns.
Arriving at a Scalable Inventory of Reusable Requirements and Components
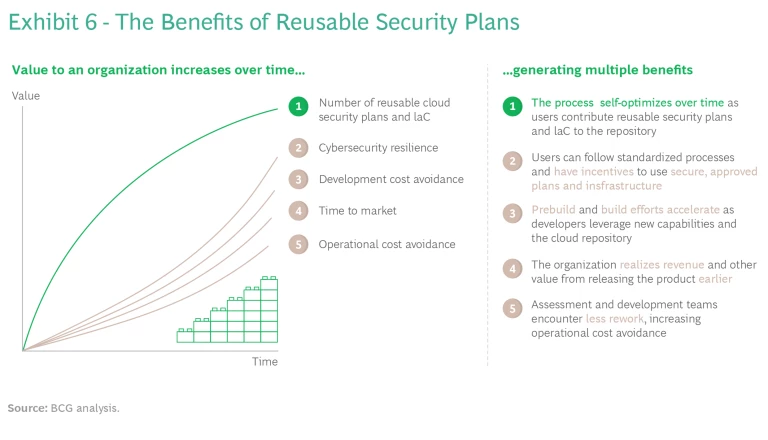
At the conclusion of the prebuild process, teams will have access to a reusable security plan that increases efficiencies and value to the business. As the number of preapproved security plans grows, the number of accelerated paths to the build phase will increase, crystallizing the value proposition of self-optimization. (See Exhibit 6.)
For development teams, once an application reaches the monitor phase, the standardized architectures permit seamless continuous monitoring and better audit and reporting activities. The result is superior cyber resilience and speed to value for app development.
Looking Forward
Businesses that adopt a holistic cloud security strategy based on Secure by Design principles will benefit from it throughout the development life cycle. Leading companies across multiple industries are adopting this approach, resulting in fewer vulnerabilities and faster responses to security concerns. Armed with this approach, teams can meet constantly changing technology needs and business objectives with confidence—instead of caution.